METAMASK PHISHER PLAYS THE VICTIM
A few days back i was having a fun conversation with Milan and Flavio and a phishing kit came up.
hxxps://www [.] back-metamask [.] com/register-login.html
THE PHISHING KIT
Typical MetaMask phish kit, nothing particularly interesting about it at face value, but i couldn't help a feeling deja vu. I started snooping around. I chose import wallet. Again, nothing particular, typical seed phrase harvesting page.
I used Ian Coleman's Mnemonic Code Converter to generate a random mnemonic phrase and "imported" my wallet. To my surprise..
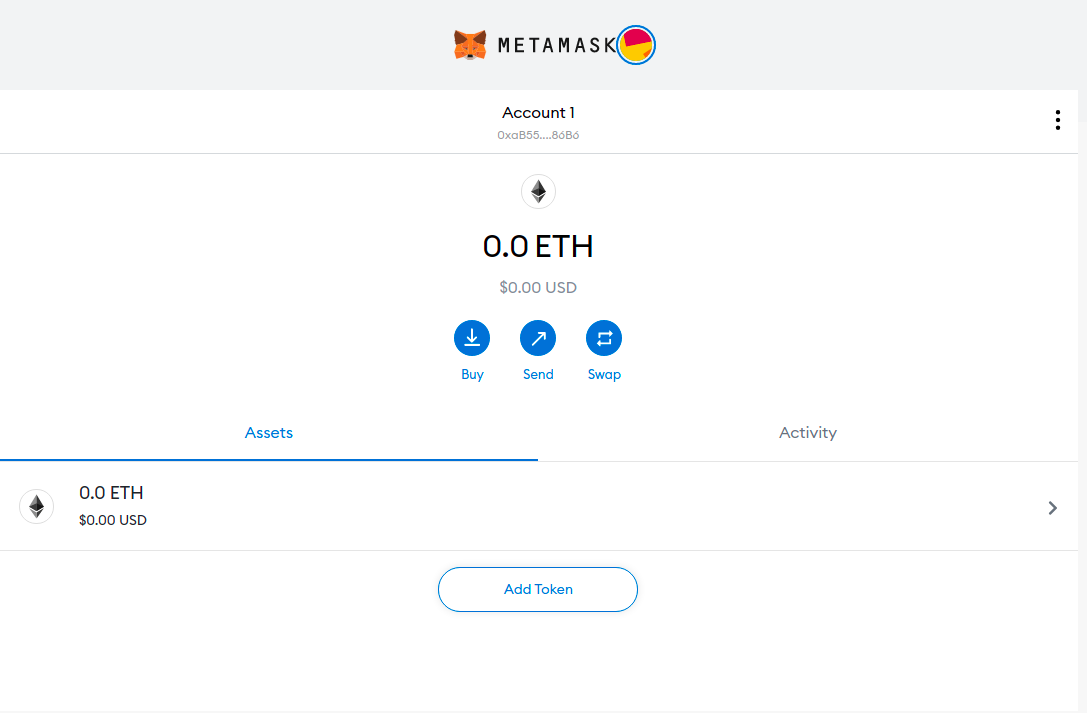
They gave me a whole wallet with all of 0 ETH 🤣. I'm still questioning this decision. From a design perspective, having a potential victim land on a page with NONE of their supposed ETH in their wallet is sure to cause them to panic.
Anyways, going through all the requests i saw that they were sending the harvested seeds through to
hxxps://www [.] back-metamask [.] com/api.php
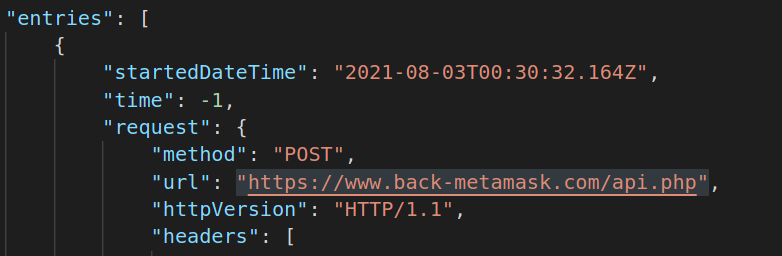
I also realised that the POST wouldn't work if the referer wasn't
hxxps://www [.] back-metamask [.] com/wallet.html
WIth all this info i wondered what if someone where to send a bunch of random mnemonic phrases? Even better, send LOADS of them at once... And "someone" did😅
DENIAL OF SERVICE
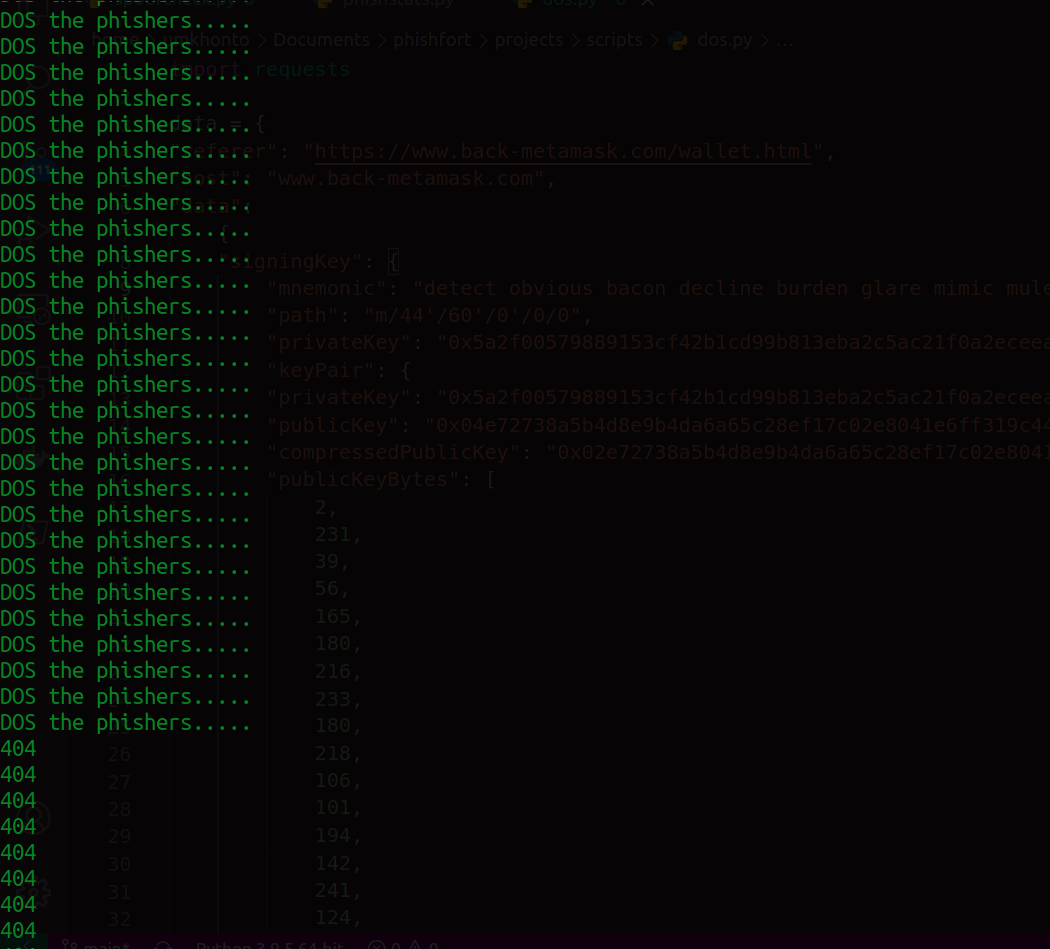
And the site went down.
It went down for some hours. it came back to life with a "new" script to collect the seeds. It was changed from
hxxps://www [.] back-metamask [.] com/api.php
to
hxxps://www [.] back-metamask [.] com/apis.php
A game of "slightly alter the name of the script" ensued. The phishers change the name of the script and the "someone" changes it as well. The phishing site had an average uptime of 5 minutes per hour.
TALKING TO THE PHISHERS
The phishers finally gave up and put up a text as their landing page. It read
"U ARE SO BAD telegram @ethpadpresaleadmin contact me"
Of course i reached out! This is how the conversation went
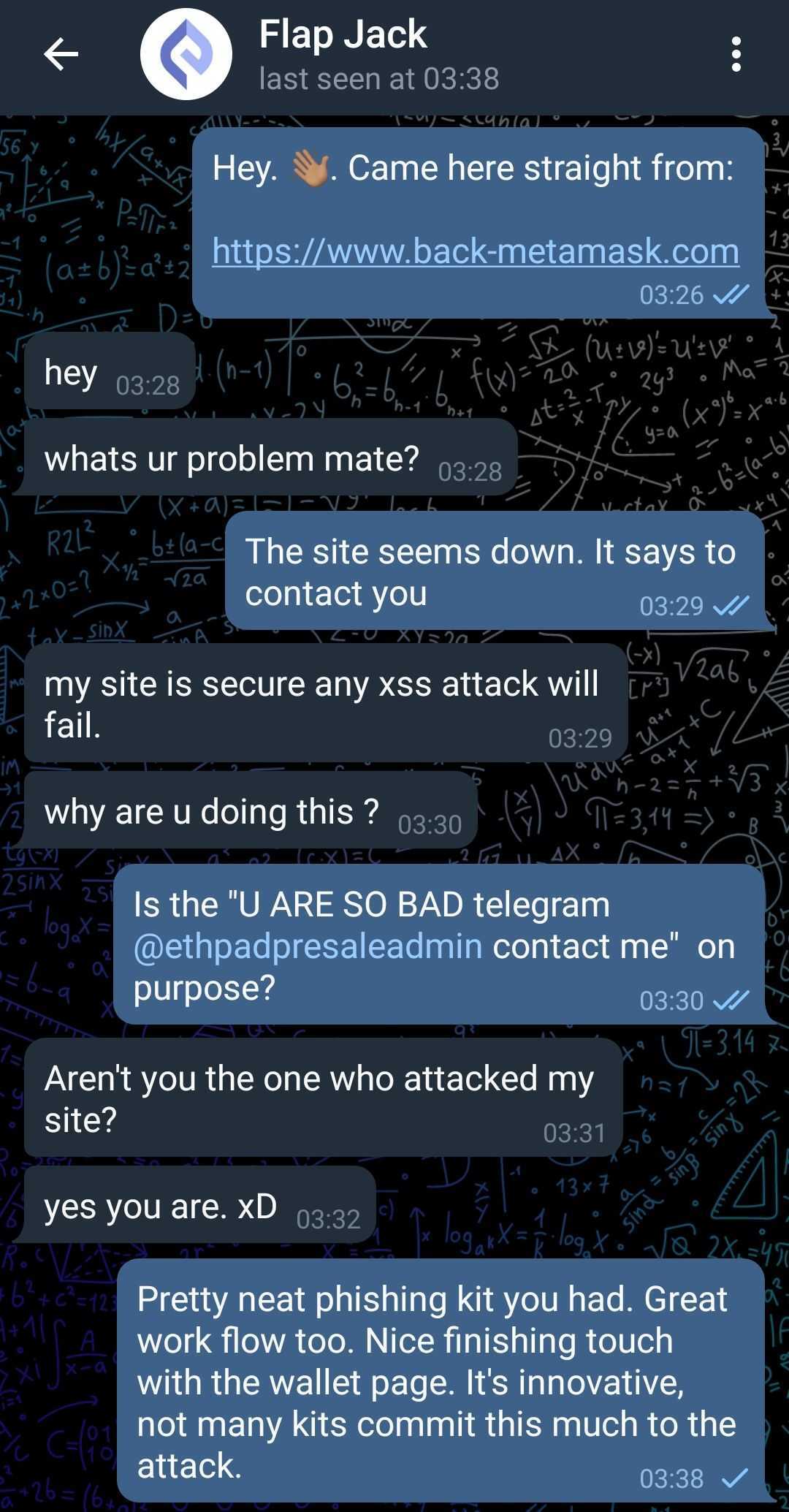
"Flap Jack" asks '..Why are u doing this?' like they are the victim 🤣🤣🤣. Staying up all night for this paid off. Another one bites the dust!
PREVIOUS ATTACKS
I scanned the domain on Virus Total and URLScan and you wouldn't believe it!
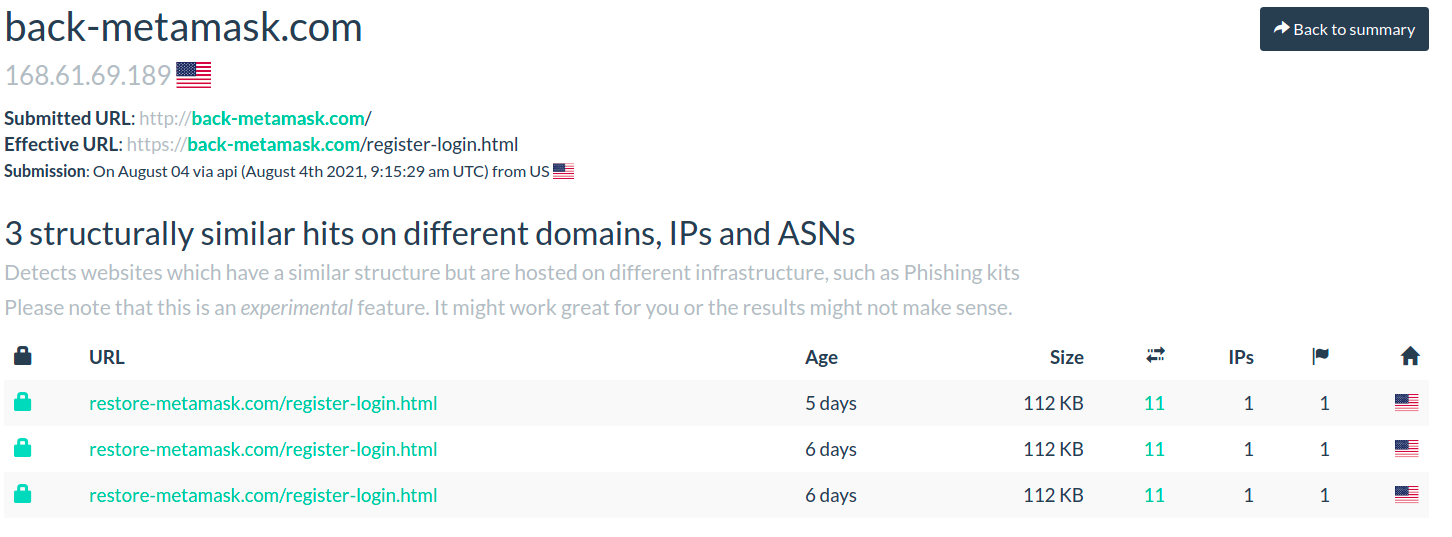
This is why i felt deja vu! I'd seen this before
hxxps://restore-metamask [.] com/register-login.html
KEY TAKEAWAYS
- DON'T EVER SHARE YOUR SECRET SEED PHRASE
- NEVER FOLLOW A LINK TO A FINANCIAL PLATFORM FROM A SOCIAL MEDIA PLATFORM - ALWAYS TYPE IT MANUALLY OR BOOKMARK IT
- LEARN WAYS OF STAYING SAFE ONLINE
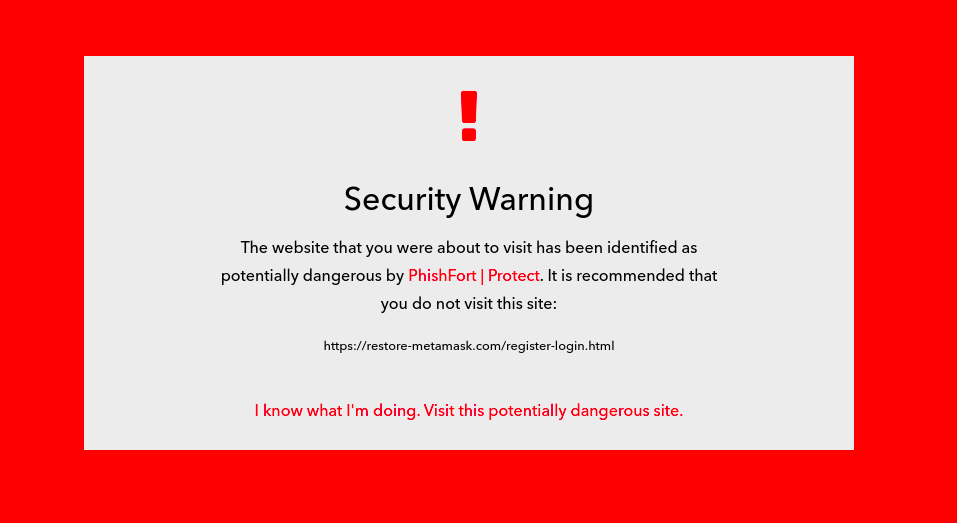
- INSTALL PHISHFORT PROTECT
- https://t.me/ethpadpresaleadmin (Flap Jack) IS A SCAMMER. REPORT THEIR ACCOUNT